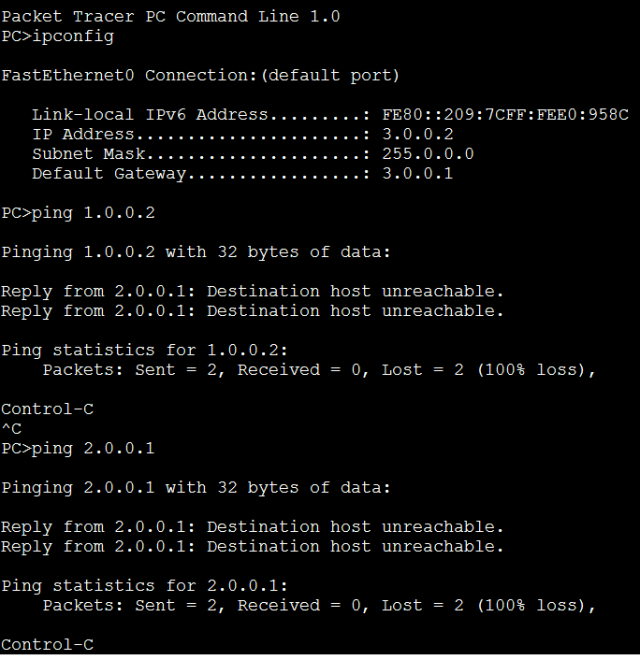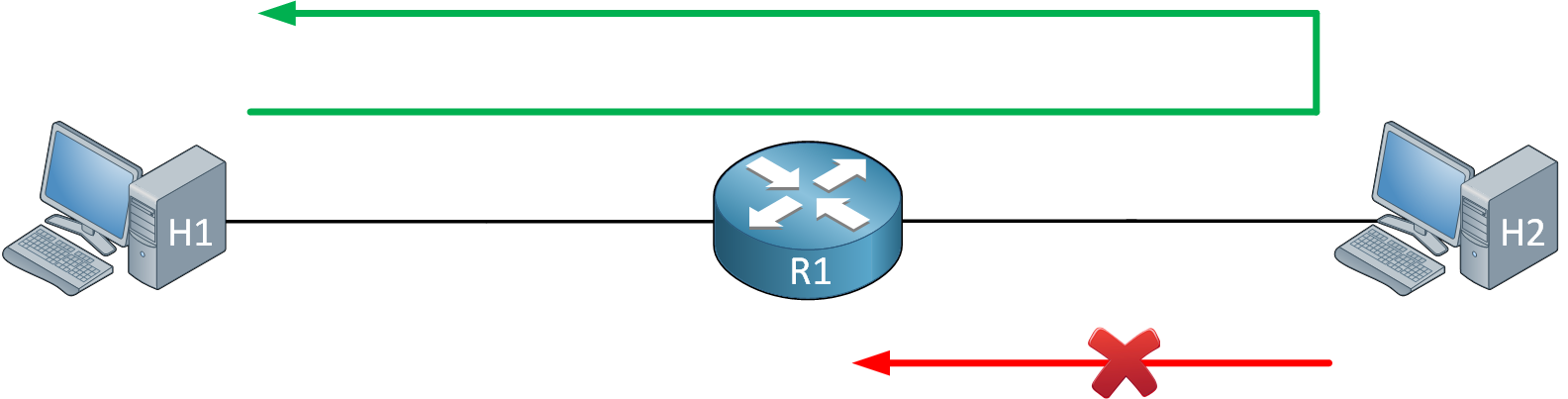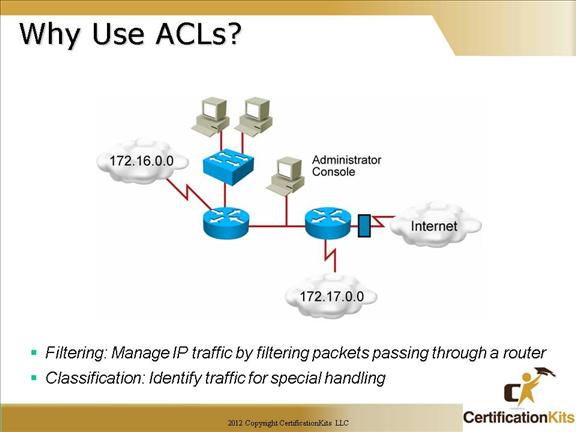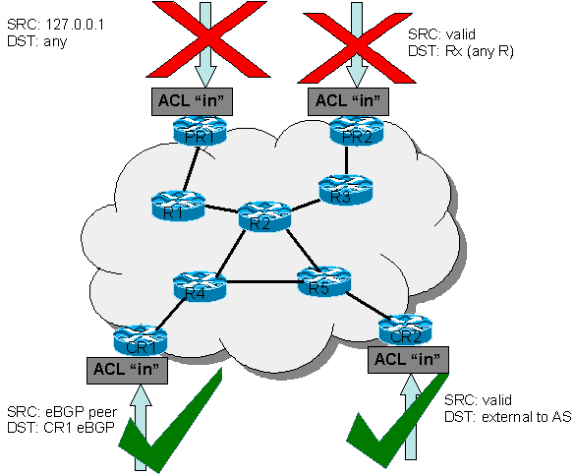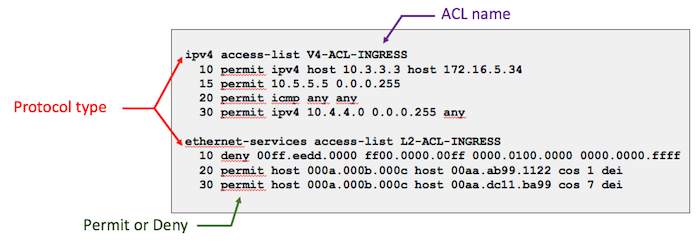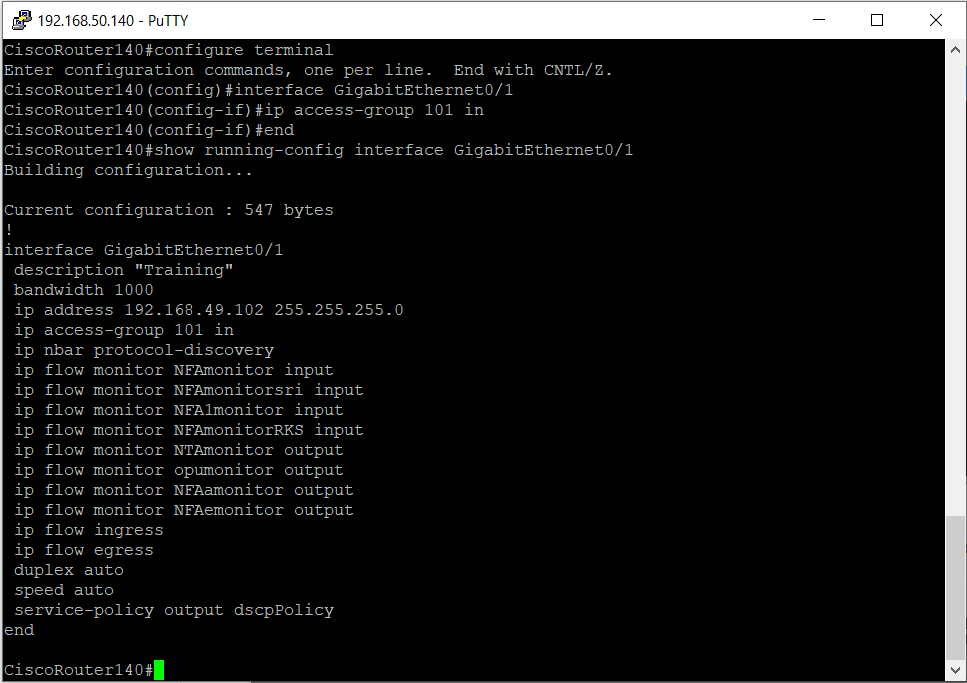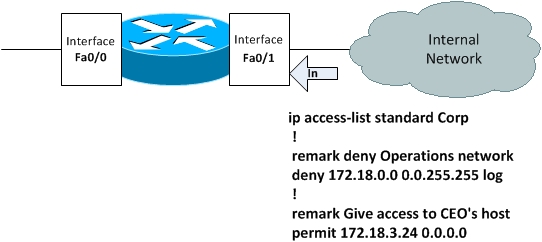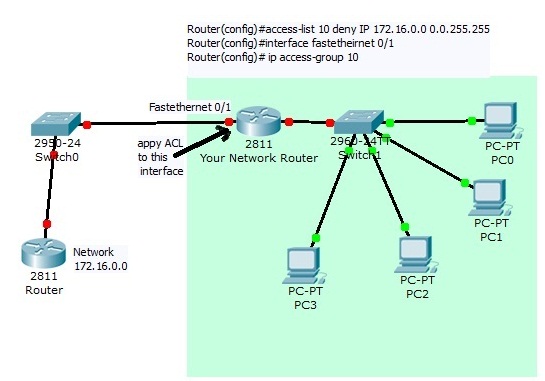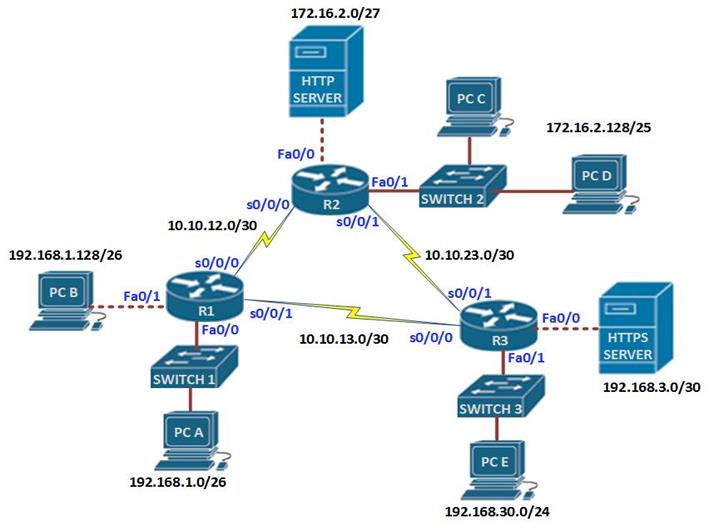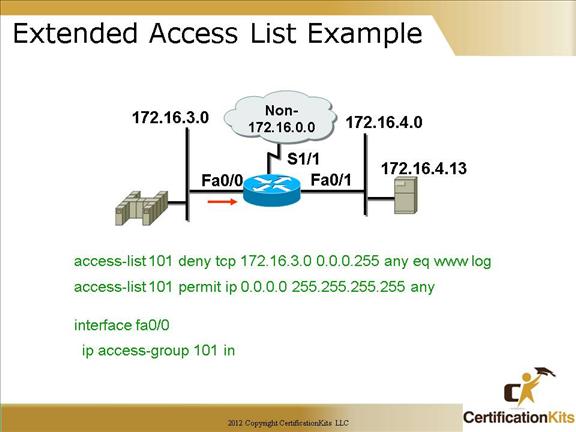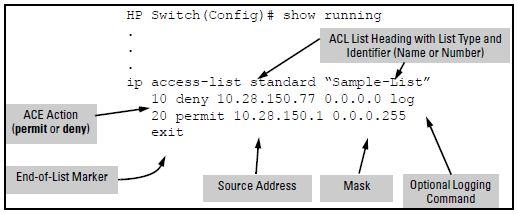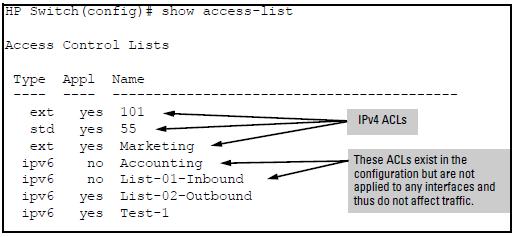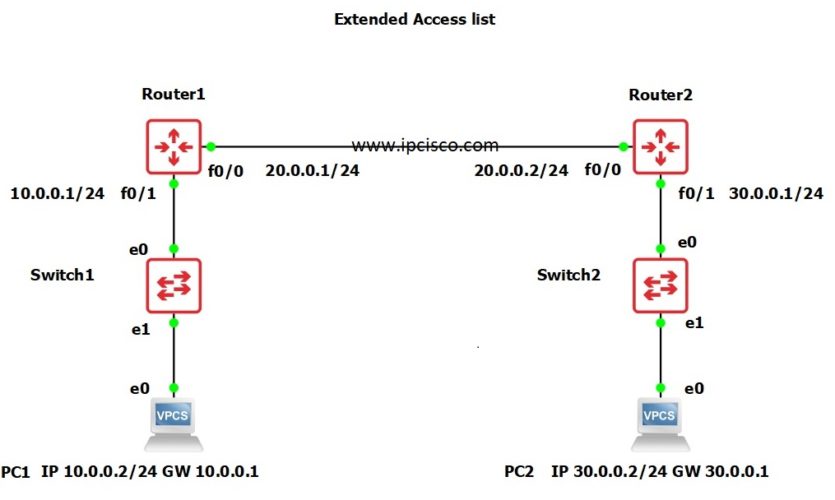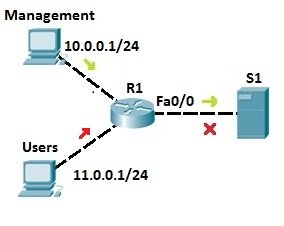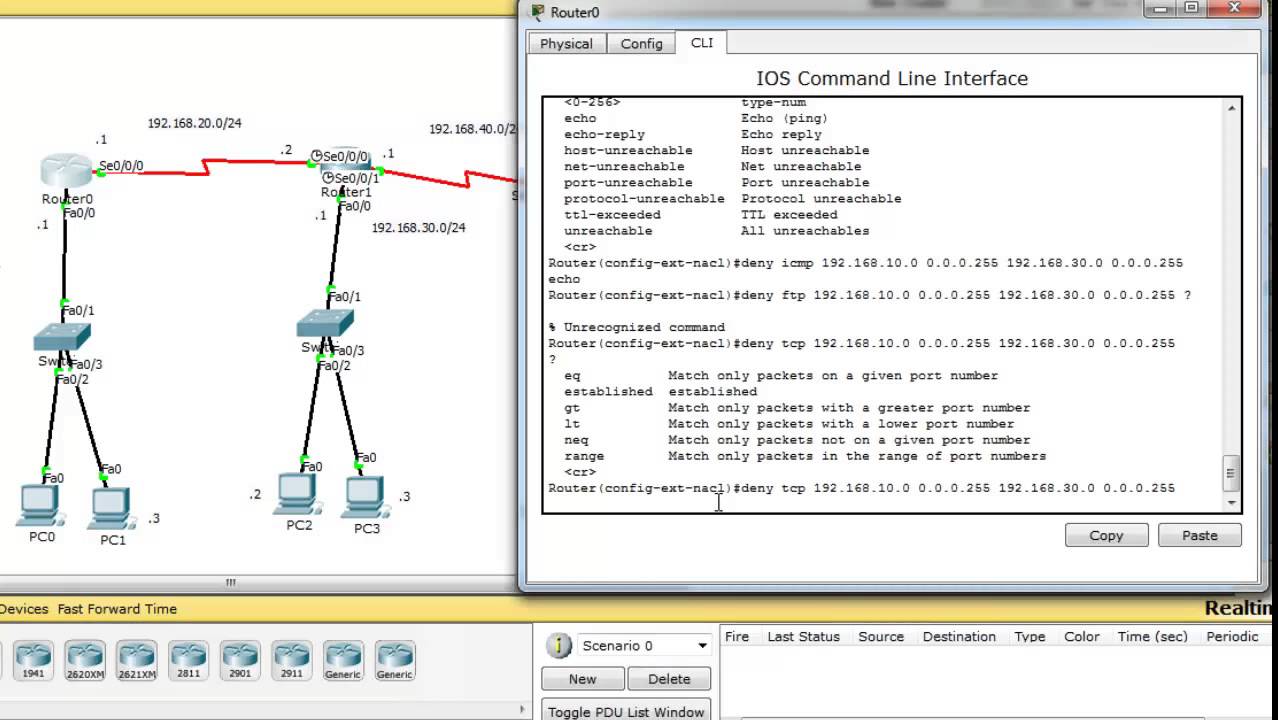
Configuring cisco extended acl / extended named access control list tutorial using packet tracer - YouTube

Configure Cisco Extended ACL/ Extended Numbered Access Control List ACL Using Packet Tracer - YouTube
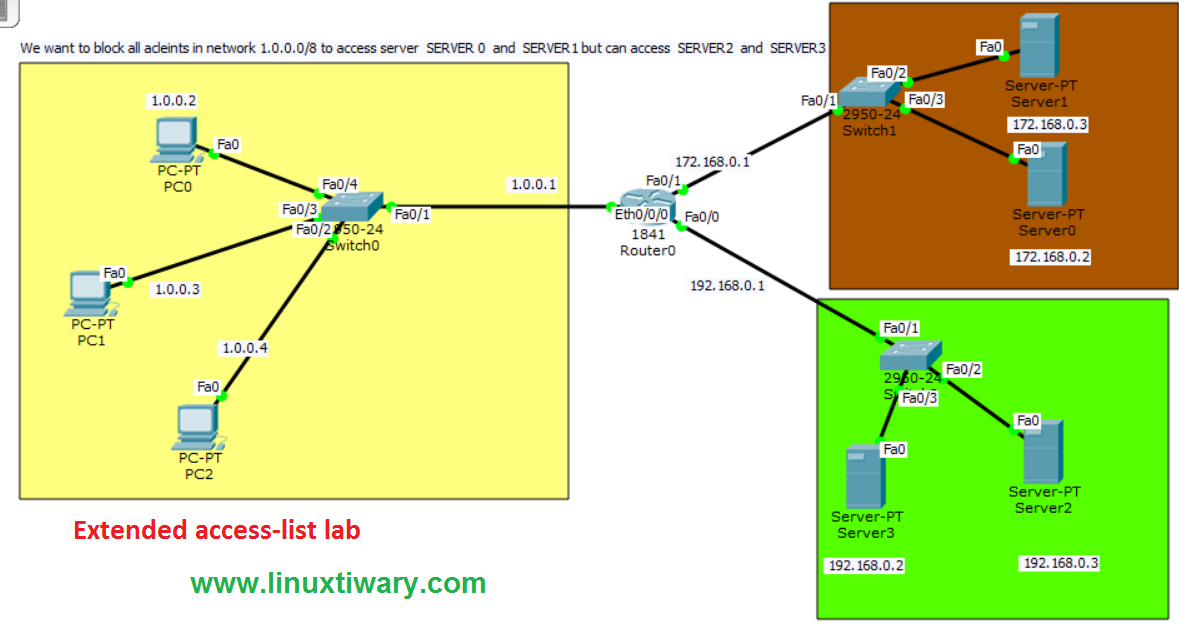
extended access-list example lab in packet tracer – Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber-Security Network-Security Online